Практически. БКС практические. Перечень лабораторных работ
 Скачать 1.44 Mb. Скачать 1.44 Mb.
|
ЛАБОРАТОРНАЯ РАБОТА № 22“ Настройка AnyConnect VPN на Cisco ASA..”(2 часа) ПМ.03 «Эксплуатация объектов сетевой инфраструктуры» МДК.03.02 Безопасность компьютерных сетей Составители(авторы) ВилковА.Н. преподаватель ФГБОУ ВО "РЭУ им. Г.В.Плеханова" 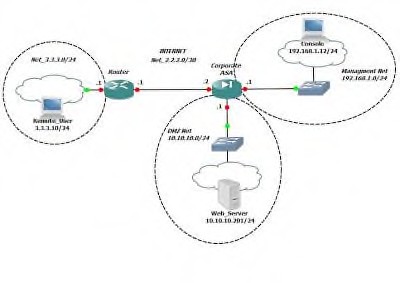 Топология сети. Настройка: ASA Version 8.0(2) command-alias exec wr copy run disk0:/.private/startup-config hostname ASA enable password 2KFQnbNIdI.2KYOU encrypted names interface Ethernet0/0 nameif outside security-level 0 ip address 2.2.2.2 255.255.255.252 interface Ethernet0/1 nameif inside security-level 100 ip address 192.168.1.1 255.255.255.0 interface Ethernet0/2 nameif dmz security-level 50 ip address 10.10.10.1 255.255.255.0 interface Ethernet0/3 shutdown no nameif no security-level no ip address interface Ethernet0/4 shutdown no nameif no security-level no ip address interface Ethernet0/5 shutdown no nameif no security-level no ip address passwd 2KFQnbNIdI.2KYOU encrypted ftp mode passive dns domain-lookup outside dns domain-lookup inside dns domain-lookup dmz access-list ADMIN extended permit ip 192.168.1.0 255.255.255.0 any access-list FOR_NAT extended permit ip 192.168.1.0 255.255.255.0 any access-list NO_NAT extended permit ip 192.168.1.0 255.255.255.0 10.10.10.0 255.255.255.0 access-list NO_NAT extended permit ip any 192.168.2.0 255.255.255.0 pager lines 24 logging enable logging asdm informational mtu outside 1500 mtu inside 1500 mtu dmz 1500 ip local pool SSL_UVPN_User_POOL 192.168.2.10-192.168.2.20 mask 255.255.255.0 no failover icmp unreachable rate-limit 1 burst-size 1 asdm image disk0:/asdm-625.bin no asdm history enable arp timeout 14400 global (outside) 1 interface nat (inside) 0 access-list NO_NAT nat (inside) 1 access-list FOR_NAT access-group ADMIN in interface inside route outside 0.0.0.0 0.0.0.0 2.2.2.1 1 timeout xlate 3:00:00 timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02 timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00 timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00 timeout uauth 0:05:00 absolute dynamic-access-policy-record DfltAccessPolicy http server enable http 192.168.1.0 255.255.255.0 inside no snmp-server location no snmp-server contact snmp-server enable traps snmp authentication linkup linkdown coldstart no crypto isakmp nat-traversal telnet timeout 5 ssh timeout 5 console timeout 0 threat-detection basic-threat threat-detection statistics access-list class-map inspection_default match default-inspection-traffic policy-map type inspect dns preset_dns_map parameters message-length maximum 512 policy-map global_policy class inspection_default inspect dns preset_dns_map inspect ftp inspect h323 h225 inspect h323 ras inspect rsh inspect rtsp inspect esmtp inspect sqlnet inspect skinny inspect sunrpc inspect xdmcp inspect sip inspect netbios inspect tftp inspect icmp service-policy global_policy global webvpn enable outside svc image disk0:/anyconnect-win-2.5.2019-k9.pkg 1 svc enable group-policy SSL_VPN internal group-policy SSL_VPN attributes vpn-tunnel-protocol l2tp-ipsec svc address-pools value SSL_UVPN_User_POOL username admin password M5soT6HHRslbuoh3 encrypted privilege 15 username UserVPN password XCZN9e/Ta3N/xJC4 encrypted privilege 0 username UserVPN attributes vpn-group-policy SSL_VPN tunnel-group SSL_VPN_Group type remote-access tunnel-group SSL_VPN_Group general-attributes address-pool SSL_UVPN_User_POOL default-group-policy SSL_VPN prompt hostname context Контрольные вопросы: Описание технологии SSL Принцип работы AnyConnect VPN |
