Основы ИБ. Фан_6363_лаб-7-23.12. Отчет по лабораторной работе 7 по дисциплине Основы информационной безопасности Тема а нализ рисков с использованием программного обеспечения RiskWatch 1
 Скачать 185.49 Kb. Скачать 185.49 Kb.
|
|
1.4 RiskWatch Parameters and Data Analysis RiskWatch Parameters This section provides the parameters selected by the Risk Analysis Team and approved by the work group for use in this analysis. The information provided includes the hours and days of operation, the number of records handled, the number of users, and the questionnaire non-compliance threshold. Name of Organization: COMPANY IBS Number/Code of Organizational Unit: 7611003390 System to be analyzed: Server for Sbis++ How many days/week does system operate: 6 How many hours/day does system operate: 9 Down time before serious consequences: 2 Time to replace Minimum Function: 0.5 Number of full-time users: 37 Data sensitivity level: 1 Security mode: C1 Orange Book Level: Proprietary Maximum $$ handled: $15,873. Interpret xx% or more as 100 xx = 60 (answers less than 85% were flagged as potential vulnerabilities) Figure 3: Summary of Parameters Data Analysis [[[ The team began the risk analysis by preparing and distributing questionnaire diskettes to 113 individuals. Included among these individuals were COMPANY IBS and NAME employees, Central Office and Regional Office System Security Officers, RACF Group Administrators, and NAME and non-COMPANY IBS users of the DATA CENTER. Although diskettes were sent to a broad range of users, the scope of the risk analysis was limited to the DATA CENTER. Each diskette contained 449 questions from which the respondents were instructed to select and answer questions in one or more functional areas. Each participant was instructed to indicate how each question (statement) applied or was perceived by the person on a scale of 0 (low) to 100 (high). If the question was not applicable or the person was unfamiliar with it, he or she was instructed to respond "N". The team received 102 completed diskettes. The response diskettes were downloaded to the RiskWatch program which processed the responses to produce a list of vulnerabilities (weaknesses) which were reviewed by the risk analysis team and validated by a review team comprised of COMPANY IBS and NAME managers and technical experts. Using the validated set of applicable vulnerabilities and a list of assets which was prepared by the risk analysis team and validated by the Director, NAME, the risk analysis team used the RiskWatch software to determine the applicable threats and annual loss expectancies and develop a set of recommended safeguards which, if implemented, could substantially reduce potential losses. ]]] VULNERABILITY AREA REPORT OVERALL COMPLIANCE: 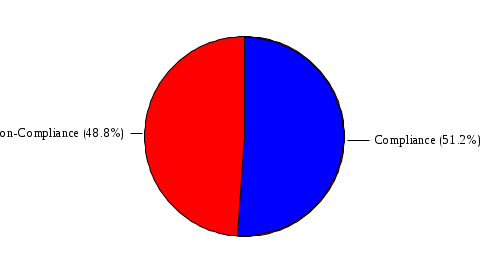 VULNERABILITY AREA: Access Control There is 100% compliance in this area of vulnerability. VULNERABILITY AREA: Accountability 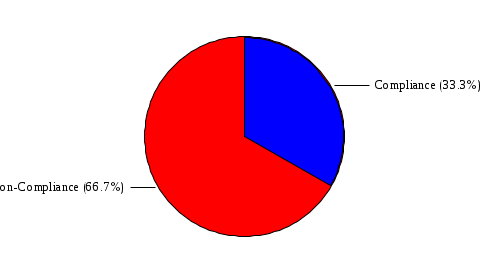 VULNERABILITY AREA: Administration There is 100% non-compliance in this area of vulnerability. VULNERABILITY AREA: Audit Trails 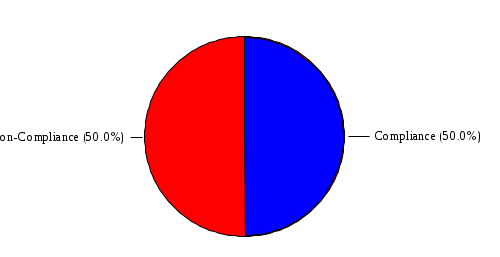 VULNERABILITY AREA: Construction There is no information available for this area of vulnerability. VULNERABILITY AREA: Contingency Plan 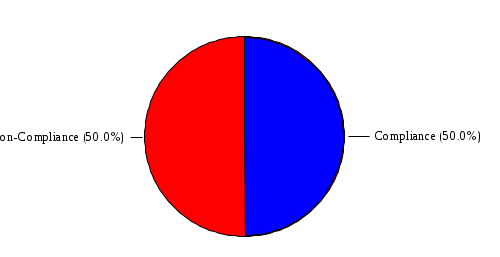 VULNERABILITY AREA: Data Integrity 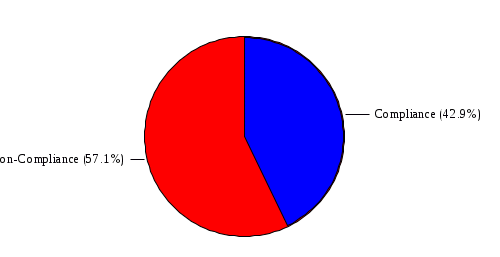 VULNERABILITY AREA: Disclosure There is 100% non-compliance in this area of vulnerability. VULNERABILITY AREA: Documentation There is 100% non-compliance in this area of vulnerability. VULNERABILITY AREA: Evaluation There is 100% compliance in this area of vulnerability. VULNERABILITY AREA: Labeling There is no information available for this area of vulnerability. VULNERABILITY AREA: Maintenance There is no information available for this area of vulnerability. VULNERABILITY AREA: Organization 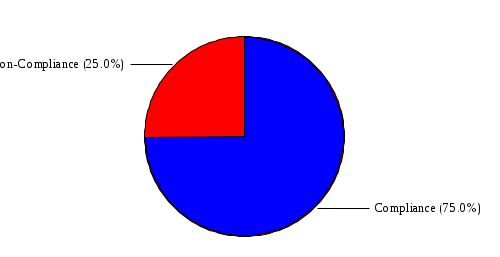 VULNERABILITY AREA: Privacy Act There is 100% compliance in this area of vulnerability. VULNERABILITY AREA: Procedures 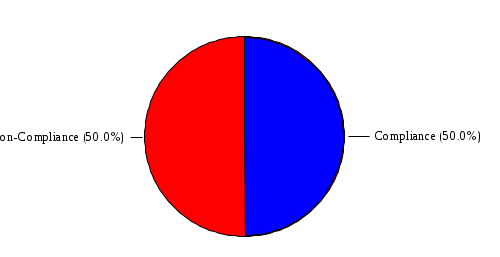 VULNERABILITY AREA: Reliability There is no information available for this area of vulnerability. VULNERABILITY AREA: Terminal Site There is no information available for this area of vulnerability. VULNERABILITY AREA: Training 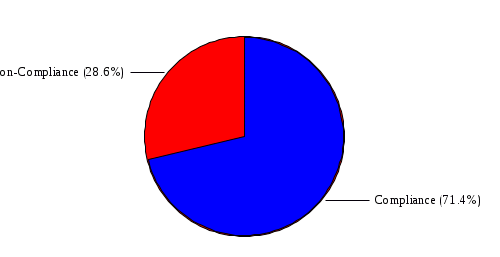 VULNERABILITY DISTRIBUTION REP0RT Those individual questions that indicate the largest degree of perceived vulnerability, as tallied from the responses, are shown below. Following each question is its associated area of vulnerability. 1. Contingency/disaster recovery plans and procedures are reviewed and tested on an annual basis? Vulnerability Area: Contingency Plan 2. Reproduction facilities and copy machines are secured or locked to prevent abuse? Vulnerability Area: Accountability 3. The organization has established effective and verifiable inspection procedures for packages, briefcases, and other materials. Vulnerability Area: Procedures 4. The network (NOS) system files are kept in a protected directory or are encrypted by the system (i.e. password files, configuration files, etc.)? Vulnerability Area: Disclosure 5. In-house developed code is adequately protected from editing by unauthorized users? Vulnerability Area: Data Integrity 6. Sufficient controls and procedures exist to ensure data is validated at each point as it moves from one medium to another? Vulnerability Area: Data Integrity 7. All code is protected from unauthorized and illegal duplication? Vulnerability Area: Data Integrity 8. The application documentation has sufficient references to internal audit and security controls to ensure validation of record accesses, to monitor unauthorized access to sensitive data, and to assess system integrity? Vulnerability Area: Documentation 9. All employees in the organization receive IT security awareness training annually? Vulnerability Area: Training 10. All new employees are scheduled for IT security awareness training immediately upon reporting to the organization? Vulnerability Area: Training 11. There are controls in place to inhibit the re-employment of employees terminated from other government agencies for cause? Vulnerability Area: Procedures 12. Additions, deletions, and modifications to financial and other sensitive programs and databases are regularly reviewed by the responsible data/application owner and/or knowledgeable independent organizational element. Vulnerability Area: Audit Trails 13. All data files are accounted for on servers or systems? Vulnerability Area: Accountability 14. The organization has written policy for the accountability, control and release of equipment and material from the facility? Vulnerability Area: Accountability 15. The agency security staff maintains documentation on the results of testing of the security protective features? Vulnerability Area: Documentation 16. The organization has staffed an effective internal audit function to be used for the development and maintenance of a system of internal controls and to provide the needed internal audit support? Vulnerability Area: Organization 17. Applications and systems have been reviewed to determine if they are sensitive, according to the integrity, availability, and confidentiality criteria? Vulnerability Area: Administration 18. Ownership of all data files have been established and files are accounted for on servers or systems? Vulnerability Area: Accountability 19. Program and/or function managers are involved in developing contingency plans for their critical business functions? Vulnerability Area: Contingency Plan 20. All system changes or new releases are tested using formal procedures and approved before being placed in operational use? Vulnerability Area: Data Integrity 21. In order to prevent loss, there are controls in place to screen candidates for employment. Vulnerability Area: Procedures 22. Controls are in place to assure that vacant positions are filled in a timely fashion. Vulnerability Area: Organization 23. Automated information processing systems are established and enforced or are under development to meet present and anticipated human resource management needs? Vulnerability Area: Organization 24. The organization has a quality assurance and performance monitoring program? Vulnerability Area: Training 25. The organization has budgeted and maintains a viable and technologically advanced training program to ensure organizational effectiveness, availability of sufficient job skills and high morale? Vulnerability Area: Training 26. Users are required to verify that the information in their files and reports is in accordance with their expectations? Vulnerability Area: Data Integrity 27. Users have proper training in recovery of data and/or backup procedures? Vulnerability Area: Training 28. All security investigation reports are maintained for at least three years or the time required by regulations? Vulnerability Area: Audit Trails 29. All data files are periodically reviewed by data/ application owners? Vulnerability Area: Data Integrity 30. Users are restricted to those applications, screens, and data they need to perform their current duty assignments? Vulnerability Area: Access Control 31. Network and system administrators have received IT security awareness training which includes agency policy, procedures, and responsibilities for network and system management? Vulnerability Area: Training 32. The organization has established confidentiality policy and has issued directives, guidelines and operating procedures? Vulnerability Area: Privacy Act 33. All data files are backed up and stored off-site in accordance with a prescribed schedule? Vulnerability Area: Contingency Plan 34. There is continuous accountability and control for all equipment and materials maintained by the organization? Vulnerability Area: Accountability 35. The organization has established a centralized authority to coordinate and approve all computer hardware and software purchases? Vulnerability Area: Organization 36. The facility has been audited for security within the last twelve months? Vulnerability Area: Evaluation 37. The training budget is sufficient to support the organization's total training needs? Vulnerability Area: Training 38. All emergency equipment, plans and procedures are tested on a periodic basis? Vulnerability Area: Contingency Plan 39. The organization uses error checking software when performing file transfers between its systems and networks and those owned and managed by other agencies and/or businesses? Vulnerability Area: Data Integrity 40. Procedures are in place and enforced to ensure that all documentation required by federal, state and local statutes are obtained and maintained in employee personnel files? Vulnerability Area: Procedures 41. The organization has a viable, verifiable system of accountability and control for all equipment and material entrusted to the organization? Vulnerability Area: Accountability The areas of vulnerability associated with the questions above are shown below, ranked according to the number of questions in each. Following the table is a chart indicating the relative importance of each area of vulnerability, as determined from the question set. Vulnerability Areas Number of Questions 1. Data Integrity 7 2. Training 7 3. Accountability 6 4. Organization 4 5. Procedures 4 6. Contingency Plan 4 7. Documentation 2 8. Audit Trails 2 9. Evaluation 1 10. Access Control 1 11. Privacy Act 1 12. Disclosure 1 13. Administration 1 14. Labeling 0 15. Maintenance 0 16. Reliability 0 17. Terminal Site 0 18. Construction 0 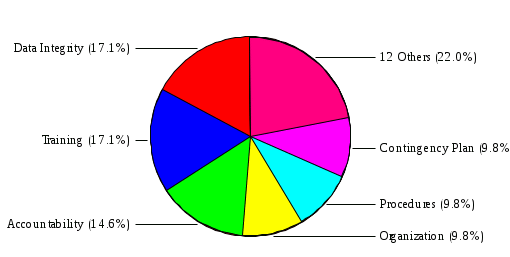 5.2 FULL SAFEGUARD REPORT This report contains information about each safeguard, including a cost benefit analysis. 5.2.1 Physical Access Control Lifetime: 3 Implementation Cost: $20,000. Annual Maintenance Cost: $500. Year Benefits Costs Disc. Ben(0.1) Disc. Cost(0.1) DB-DC(0.1) 1 $3,501. $20,000. $3,182. $18,181. $-14,998. 2 $3,501. $500. $2,893. $413. $2,480. 3 $3,501. $500. $2,630. $375. $2,254. Sum of discounted benefits (0.05): $9,533. Sum of discounted benefits (0.1): $8,705. Sum of discounted benefits (0.15): $7,993. Sum of discounted costs (0.05): $19,931. Sum of discounted costs (0.1): $18,969. Sum of discounted costs (0.15): $18,097. Benefit Cost Ratio (0.05): 0.48 Benefit Cost Ratio (0.1): 0.46 Benefit Cost Ratio (0.15): 0.44 Return On Investment (0.05): 0.16 Return On Investment (0.1): 0.15 Return On Investment (0.15): 0.15 Payback period (0.05): 0 Payback period (0.1): 0 Payback period (0.15): 0 5.2.2 Application Controls Lifetime: 3 Implementation Cost: $500. Annual Maintenance Cost: $50. Year Benefits Costs Disc. Ben(0.1) Disc. Cost(0.1) DB-DC(0.1) 1 $15,148. $500. $13,770. $454. $13,316. 2 $15,148. $50. $12,518. $41. $12,477. 3 $15,148. $50. $11,380. $37. $11,343. Sum of discounted benefits (0.05): $41,250. Sum of discounted benefits (0.1): $37,668. Sum of discounted benefits (0.15): $34,586. Sum of discounted costs (0.05): $564. Sum of discounted costs (0.1): $532. Sum of discounted costs (0.15): $503. Benefit Cost Ratio (0.05): 73.05 Benefit Cost Ratio (0.1): 70.62 Benefit Cost Ratio (0.15): 68.42 Return On Investment (0.05): 24.35 Return On Investment (0.1): 23.54 Return On Investment (0.15): 22.81 Payback period (0.05): 1 Payback period (0.1): 1 Payback period (0.15): 1 5.2.3 Audit Trails Lifetime: 5 Implementation Cost: $1,000. Annual Maintenance Cost: $500. Year Benefits Costs Disc. Ben(0.1) Disc. Cost(0.1) DB-DC(0.1) 1 $3,967. $1,000. $3,606. $909. $2,697. 2 $3,967. $500. $3,278. $413. $2,865. 3 $3,967. $500. $2,980. $375. $2,604. 4 $3,967. $500. $2,709. $341. $2,368. 5 $3,967. $500. $2,463. $310. $2,152. Sum of discounted benefits (0.05): $17,174. Sum of discounted benefits (0.1): $15,036. Sum of discounted benefits (0.15): $13,296. Sum of discounted costs (0.05): $2,638. Sum of discounted costs (0.1): $2,348. Sum of discounted costs (0.15): $2,108. Benefit Cost Ratio (0.05): 6.50 Benefit Cost Ratio (0.1): 6.40 Benefit Cost Ratio (0.15): 6.30 Return On Investment (0.05): 1.30 Return On Investment (0.1): 1.28 Return On Investment (0.15): 1.26 Payback period (0.05): 1 Payback period (0.1): 1 Payback period (0.15): 1 5.2.4 Classification Markings Lifetime: 3 Implementation Cost: $500. Annual Maintenance Cost: $50. Year Benefits Costs Disc. Ben(0.1) Disc. Cost(0.1) DB-DC(0.1) 1 $1,920. $500. $1,745. $454. $1,290. 2 $1,920. $50. $1,586. $41. $1,545. 3 $1,920. $50. $1,442. $37. $1,404. Sum of discounted benefits (0.05): $5,227. Sum of discounted benefits (0.1): $4,773. Sum of discounted benefits (0.15): $4,382. Sum of discounted costs (0.05): $564. Sum of discounted costs (0.1): $532. Sum of discounted costs (0.15): $503. Benefit Cost Ratio (0.05): 9.26 Benefit Cost Ratio (0.1): 8.95 Benefit Cost Ratio (0.15): 8.67 Return On Investment (0.05): 3.09 Return On Investment (0.1): 2.98 Return On Investment (0.15): 2.89 Payback period (0.05): 1 Payback period (0.1): 1 Payback period (0.15): 1 5.2.5 Contingency Plan Lifetime: 2 Implementation Cost: $1,000. Annual Maintenance Cost: $200. Year Benefits Costs Disc. Ben(0.1) Disc. Cost(0.1) DB-DC(0.1) 1 $158. $1,000. $143. $909. $-765. 2 $158. $200. $130. $165. $-34. Sum of discounted benefits (0.05): $293. Sum of discounted benefits (0.1): $273. Sum of discounted benefits (0.15): $256. Sum of discounted costs (0.05): $1,133. Sum of discounted costs (0.1): $1,074. Sum of discounted costs (0.15): $1,020. Benefit Cost Ratio (0.05): 0.26 Benefit Cost Ratio (0.1): 0.26 Benefit Cost Ratio (0.15): 0.25 Return On Investment (0.05): 0.13 Return On Investment (0.1): 0.13 Return On Investment (0.15): 0.13 Payback period (0.05): 0 Payback period (0.1): 0 Payback period (0.15): 0 |
