Введение настоящее учебное пособие предназначено для студентов, обучающихся по направлениям 09
 Скачать 366.09 Kb. Скачать 366.09 Kb.
|
robots in medicineIn modern medicine robots play an increasing role, which requires a new kind of training for the next generation of doctors. Usage of robots reduces hospital stays and improves patients’ prognosis and saves costs. Mechanical replacements for missing limbs and organs that can interact with the human organic system are a long-standing goal of the medical community. Research into replacement of hearts, limbs, eyes, ears and other organs offers hope for the development of effective implanted devices and replacement limbs that can function for long periods of time. Robotic devices can also provide assistance to people with severe restrictions on movement, in many cases allowing them at least some capability to move around or nearby their homes. Robot NursyBoy intended to prevent or reduce medical errors by the patient. This robot is not just beeps when need to take medicines, but also delivers an additional notification to the patient on ad hoc bracelet on the arm. This allows the patient to know when need to take the necessary dose of medication, if the pills are still in the compartment, the device shows that the drug was not taken, and recalls that the reception was done. Patients will not be able to skip taking medications because this device is designed in such a way that will emit a loud noise and rattling on hand as long as the drugs will not be accepted. When an emergency occurs the robot will automatically connect by means of video voice communication with the medical center or family finding and viewing the patient (communication Wi-Fi or telephone). After receiving medicines on the LCD touch monitor is displaying the special directions of how it looks like and how it is necessary to take it – for example, before or after a meal, or diluted in water. Artificial Eye could help the blind see again. Artificial Eye Gaze in the shape of the natural form of human eye. Artificial eye heralds the emergence of new small-footprint devices with a wide field of view and low distortion. The resulting picture is indistinguishable from the image seen by human eye. So it will be possible to transfer the images directly into the brain of blind people with help of electronic eyeball. This development will allow to solve the problem for blind people and to make a new step in science, having opened a new direction in personal video perception systems in the field of volumetric video. This is a completely new idea of developing a flat lens with a tiny camera that could revolutionize the eyeball. Curved glass can bend the light coming from many angles in such a way that it all ends up at the same focal point, an electric sensor. The sensors and the lens only focus one wavelength of light that can handle normal color images. The camera would transmit images to a nerve-stimulating chip at the back of the eye, resulting in a complete electronic vision system, translate images from camera into electrical impulses that can be understand by the nerves inside the brain. Chip to generate a signal which is as close as possible looks like a real retina eye. Wherever you change the input, the brain will adapt over time. The digital information picked up from the camera is sent to a thin film. This thin film is surgically implanted in the back of the patient’s eye. The electrical signals stimulate the nerves in the retina and that make the patient able to see. Task 8. Answer the following questions: 1. How do robots penetrate in medicine? 2. What is the main function of Robot NursyBoy? 3. How does Artificial Eye help blind people? 4. Have you heard about any other robots helping sick, elderly or disabled people? Task 9. Find in the text synonyms and antonyms for the following words. The words are given in the same order as in the text.
Task 10. Match the following words from the text with their definitions:
Task 11. Complete the sentences using the following words or phrases from the text in the correct form: to stimulate, to be, will be, digital, to look, to develop, to occur. 1. Chip to generate a signal which is as close as possible … like a real retina eye. 2. This is a completely new idea … a flat lens with a tiny camera that could revolutionize the eyeball. 3. It … possible to transfer the images directly into the brain of blind people. 4. The … information picked up from the camera is sent to a thin film. 5. The electrical signals … the nerves in the retina. 6. The resulting picture … indistinguishable from the image seen by human eye. 7. When an emergency … the robot will automatically connect with the medical center or family. Task 12. Find some information about the latest robots in medicine on the Internet and prepare a short report. Task 13. Study the words and phrases from text C:
. Task 14. Read and translate the plot of a science fiction drama film A.I. Artificial Intelligence (2001) directed by Steven Spielberg. Have you seen this film?  In the late 22nd century in Madison, David, a Mecha robot that resembles a human child and is programmed to display love for his owners, is given to Henry Swinton and his wife Monica. Their son Martin, after contracting a rare disease, is not expected to recover. Monica feels uneasy with David, but eventually warms to him and activates his imprinting protocol, causing him to have an enduring childlike love for her. Martin is cured of his disease and brought home. As he recovers, he grows jealous ofDavid. He tricks David into entering the parents' bedroom at night and cutting off a lock of Monica's hair. Later at a pool party, one of Martin's friends pokes David with a knife, activating David's self-protection programming. David grabs Martin and they fall into the pool. Martin is saved from drowning, but Henry persuades Monica to return David to his creators for destruction. Instead, she abandons David with his robotic teddy bear Teddy in the forest. She tells him to find other unregistered Mecha who can protect him. David is captured for an anti-Mecha "Flesh Fair" where unlicensed robots are destroyed before cheering crowds. David is placed on a platform with Gigolo Joe, a male sex worker Mecha who is on the run. Before destruction, the crowd, thinking David is a real boy, begins booing. In the chaos, David and Joe escape. Joe agrees to help David find Blue Fairy from The Adventures of Pinocchio who, he believes, can turn him into a real boy. Joe and David meet "Dr. Know", a holographic answer engine and then Professor Hobby, David’s creator, who tells him he was built in the image of the professor's dead son David. The engineers are thrilled by his ability to have a will without being programmed. Disheartened, David lets himself fall from a ledge of the building but rescued by Joe, flying an amphibicopter. David tells Joe he saw the Blue Fairy underwater, and wants to go down to meet her. Joe is captured by the authorities but before he is pulled up, he activates the amphibicopter's dive function for David, telling him to remember him for he declares "I am, I was." David and Teddy dive to see the Fairy, which turns out to be a statue. David repeatedly asks the Fairy to turn him into a real boy. Eventually the ocean freezes. Two thousand years later humans are extinct and the Mecha have evolved into an advanced silicon-based form called Specialists. They find David and Teddy, and discover they are original Mecha who knew living humans. The Specialists revive David and use his memories to reconstruct the Swinton home. David asks the Specialists if they can make him human, but they cannot. However, he insists they recreate Monica from DNA from the lock of her hair, which Teddy has kept. The Mecha warn David that the clone can live for only a day, and that the process cannot be repeated. David spends the next day with Monica and Teddy. Before she drifts off tosleep, Monica tells David she has always loved him. Task 15. Translate the following word combinations from the text: imprinting protocol, unlicensed robots, to fly an amphibicopter, to activate the function, to recreate someone from DNA, self-protection programming, to reconstruct smth., holographic answer engine, to resemble a human child, to turn someone into a real boy Task 16. Why do you think the plot is written in the Present tense? Find all examples of the Passive voice (is programmed) and then make up 5 sentences with them. (You can change the tense!) Task 17. Have you seen any other sci-fi movies? Talk about your favourite movie of this kind. Unit 6 VIRTUAL REALITY VS AUGMENTED REALITY Task 1. Match the following English words and phrases from text A with their Russian equivalents:
Task 2. Read and translate text A: VIRTUAL REALITY Virtual reality (VR) is a realistic three-dimensional environment that is created with a mixture of interactive hardware and software, and presented to the user in such a way that it is accepted as a real environment. It aims to achieve total immersion. Total immersion means that the sensory experience feels so real that we forget it is a virtual-artificial environment. VR literally makes it possible to experience anything, anywhere, anytime. The key elements of VR are: virtual world immersion, sensory feedback interactivity. A virtual world is a three-dimensional environment that is often realized through a medium where one can interact with others and create objects as part of that interaction. Here visual perspectives are responsive to changes experienced in the real world. Virtual reality immersion is the perception of being physically present in a non-physical world. Mental immersion is a deep mental state of engagement while physical immersion is exhibited physical engagement in a virtual environment. VR requires such senses as vision, hearing, touch and more to be simulated. Sensory feedback is achieved through integrated hardware and software. Interaction is crucial for VR. If the virtual environment responds to a user’s action in a natural manner, excitement and senses of immersion will remain. If the virtual environment cannot respond quick enough, the human brain will quickly notice it and the senseof immersion will diminish. Task 3. Answer the following questions: 1. What does Virtual reality mean? 2. What is the aim of VR? 3. What does total immersion mean? 4. What are the key elements of VR? 5. Why is interaction crucial for VR? Task 4. Match the following words from the text with their definitions:
Task 5. Use the following derivatives to complete the sentences: to interact interactive interaction 1. You should expect a very high level of……..with the system. 2. The main problem here is how people would……. . 3. One of the best things about the book is its………infographics. Make up your own sentences with these derivatives: To simulate simulation simulator To immerse immersion immersive To respond response responsive Task 6. Match the following English words and phrases from text B with their Russian equivalents:
Task 7. Read and translate text B: AUGMENTED REALITY Augmented reality (AR) is an enhanced version of reality where live direct or indirect views of physical real world environments are augmented with superimposed computer-generated images over a user’s view of the real world. The origin of the word “augmented” is “augment” which means to add. In the case of AR graphics, sounds and touch feedback are added into user’s natural world. Unlike virtual reality, which requires a user to inhabit an entirely virtual environment, augmented reality simply overlays virtual information on top of existing natural environment. As a result AR users experience a new and improved world where virtual information is used as a tool to provide assistance in everyday activities. From a technological point of view this is done by overlaying projected images on top of a pair of see-through goggles or glasses. Augmented reality devices are often self-contained – they don’t need a cable or desktop computer to function. Augmented realities can be displayed not only on screens and monitors but also on handheld devices or glasses and even contact lenses. The key components to augmented reality devices are: sensors and cameras projection processing reflection. Sensors (they gather a user’s real world interactions) and cameras (they visually scan to collect data) are usually located on the outside of the augmented reality device. The device takes this information and formulates a digital model to determine appropriate output. A projector is found on a forward and outward-facing position on wearable augmented reality headsets. It can essentially turn any surface into an interactive environment. As augmented reality devices are mini-supercomputers packed into tiny wearable devices, they require significant computer processing power. Apart from a CPU, a GPU, flash memory, GPS, Bluetooth/Wifi microchip and so on, advanced AR devices also utilize an accelerometer, a gyroscope and a magnetometer to provide for truly immersive experience. Mirrors reflecting incoming light are used in AR devices to assist with image alignment to the user’s eye. Augmented reality devices are controlled by touch a pad or voicecommands. The touch pads are somewhere on the device that is easily reachable. Voice commands work very similar to the way they do on our smartphones. Task 8. Answer the following questions: 1. What is augmented reality? 2. What is the origin if the word “augmented”? 3. What happens to virtual information in AR? 4. Can augmented realities be displayed only on screens and monitors? 5. What are the key components to augmented reality devices? 6. How do sensors work? 7. What are mirrors used for? 8. How are augmented reality devices controlled? Task 9. Match the following words from the text with their definitions:
Task 10. Read the following descriptions and decide which one is about accelerometer gyroscope magnetometer 1. …… is used to measure the tilt and orientation of your head 2. ………is used to function as a compass and figure out which direction your head is pointing. 3………..is used to measure the speed in which your head is moving. It is said that they all provide for truly immersive experience. Can you explain what it means? Task 11. Look at the following words from the text. What parts of speech are they? How are they formed? Can you think of more examples? Wearable Reachable Handheld Self-contained Overlaying Task 12. Match the following English words and phrases from text C with their Russian equivalents:
Task 13. Read and translate text C: AUGMENTED REALITY VS. VIRTUAL REALITY? Both Augmented reality and Virtual reality are inverse reflections of one in another with what each technology seeks to accomplish and deliver for the user. Virtual reality offers a digital recreation of a real life setting, while augmented reality delivers virtual elements as an overlay to the real world. These realities may be similar and different but it is not always virtual reality vs. augmented reality. Both technologies enable experiences that are becoming more commonly expected and sought after for entertainment purposes. While in the past they seemed merely a figmentof a science fiction imagination, new artificial worlds come to life under the user’s control, and deeper layers of interaction with the real world are also achievable. Leading tech moguls are investing in developing new adaptations, improvements, and releasing more and more products and apps that support these technologies for the increasingly savvy users. Augmented reality enhances experiences by adding virtual components such as digital images, graphics, or sensations as a new layer of interaction with the real world. Contrastingly, virtual reality creates its own reality that is completely computer generated and driven. Virtual Reality is usually delivered to the user through a head-mounted, or hand-held controller. This equipment connects people to the virtual reality, and allows them to control and navigate their actions in an environment meant to simulate the real world. Augmented reality is being used more and more in mobile devices such as laptops, smart phones, and tablets to change how the real world and digital images, graphics intersect and interact. But they do not always operate independently of one another, and in fact are often blended together to generate an even more immersingexperience. For example, haptic feedback – which is the vibration and sensation added to interaction with graphics – is considered an augmentation. However, it is commonly used within a virtual realitysetting in order to make the experience more lifelike through touch. Task 14. Are these sentences True or False: 1. Digital recreation of a real life setting is offered by VR. 2. Augmented reality is completely different from virtual reality. 3. AR creates computer-driven reality. 4. Deeper layers of interaction are likely to achieve. 5. Head-mounted and hand-held controllers allow people to control their lives. Task 15. Match the following words from the text with their definitions:
Task 16. Talk about the differences between augmented and virtual realities using this picture. 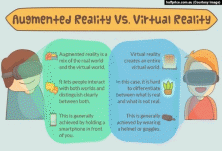 Task 17. Read the statements and decide whether you agree or disagree with them. Say to what extent you agree or disagree and try to give your arguments: -agree strongly -agree -not sure -disagree -disagree strongly Big Brother is watching you… 1. It’s OK for data about personal shopping habits to be collected and shared. 2. The government should have the right to record everyone’s internet activities. 3. Biometric identity cards would be useful in the fight against terrorism. 4. We need more traffic cameras with number-plate recognition to make the roads safer. 5. I’m in favour of CCTV (close circuit television) cameras because they help to reduce crime. Task 18. VR stands for Virtual Reality. What do the following abbreviations stand for? Look up in the abbreviations list at the end of the book. WWW TCP/IP ICT CPU GPS LCD IAS Unit 7 ASPECTS OF INFORMATION SECURITY Task 1. Match the following English words and phrases from text A with their Russian equivalents:
Task 2. Read and translate text A. INFORMATION SECURITY Information security, sometimes shortened to InfoSec, is the practice of defending information from unauthorized access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction. It is a general term that can be used regardless of the form the data may take (electronic, physical, etc...) Governments, military, corporations, financial institutions, hospitals, and private businesses amass a great deal of confidential information about their employees, customers, products, research and financial status. Most of this information is now collected, processed and stored on electronic computers and transmitted across networks to other computers. Should confidential information about a business' customers or finances or new product line fall into the hands of a competitor or a black hat hacker, such a breach of security could lead to exploited data and/or information, exploited staff/personnel, fraud, theft, and information leaks. Also, irreparable data loss and system instability can result from malicious access to confidential data and systems. Protecting confidential information is a business requirement, and in many cases also an ethical and legal requirement. For the individual, information security has a significant effect on privacy, which is viewed very differently in different cultures. The field of information security has grown and evolved significantly in recent years. There are many ways of gaining entry into the field as a career. It offers many areas for specialization including: securing network(s) and allied infrastructure, securing applications and databases, security testing, information systems auditing, business continuity planning, etc. The CIA triad (confidentiality, integrity and availability) is one of the core principles of information security. Confidentiality refers to preventing the disclosure of information to unauthorized individuals or systems. For example, a credit card transaction on the Internet requires the credit card number to be transmitted from the buyer to the merchant and from the merchant to a transaction processing network. The system attempts to enforce confidentiality by encrypting the card number during transmission, by limiting the places where it might appear (in databases, log files, backups, printed receipts, and so on), and by restricting access to the places where it is stored. If an unauthorized party obtains the card number in any way, a breach of confidentiality has occurred. Confidentiality is necessary for maintaining the privacy of the people whose personal information is held in the system. Integrity. In information security, data integrity means maintaining and assuring the accuracy and consistency of data over its entire life-cycle. This means that data cannot be modified in an unauthorized or undetected manner. This is not the same thing as referential integrity in databases, although it can be viewed as a special case of Consistency as understood in the classic ACID (automated classification and interpretation of data) model of transaction processing. Integrity is violated when a message is actively modified in transit. Information security systems typically provide message integrity in addition to data confidentiality. Availability. For any information system to serve its purpose, the information must be available when it is needed. This means that the computing systems used to store and process the information, the security controls used to protect it. and the communication channels used to access it must be functioning correctly. High availability systems aim to remain available at all times, preventing service disruptions due to power outages, hardware failures, and system upgrades. Ensuring availability also involves preventing denial-of-service attacks. Task 3. Answer the following questions: 1. What is the definition of Information security? 2. Which confidential information is stored on electronic computers? 3. What can the information leakage lead to? 4. Can you give an example of black hat hackers activities? 5. Could you briefly explain the meanings of CIA triad? 6. Do you think Information security is growing profession? 7. Do you think it is well-paid sphere for a young graduate? Task 4. Match the following words from the text with their definitions:
Task 5. Find the equivalents in the text: несанкционированный доступ; вредоносный доступ; финансовые организации; частный бизнес; финансовое положение; попасть в руки конкурента; используемые в собственных интересах данные; неустойчивость системы; иметь значительное влияние; распечатанная квитанция; запрет доступа; точность и непротиворечивость информации; сбой в работе оборудования; хакерская атака типа «отказ в обслуживании» Task 6. Insert the missing words and word combinations into the following sentences: unauthorized access; informationsecurity; cyber attacks; confidential information; fraud, to restrict, disclosure, to prevent, requirement. Sometimes you should change the form of the words: 1. Your prompt action ….. a serious accident. 2. …. is a stable and growing profession. 3. They were sent to prison for ….. . 4. Our company conference room is very small, so we have to … the number of people we invite to the meeting. 5. If you disclose this … , you may lose your job. 6. The computer programs, and in many cases the computers that process the information, must be protected from ….. . 7. Educational and professional …. for IT specialists are really high in modern world. 8. A …. is deliberate exploitation of computer systems, technology-dependent enterprises and networks. 9. Information … enables an attacker to gain valuable information about a system. Task 7. Match the following English words and phrases from text B with their Russian equivalents:
Task 8. Read and translate text B. NEW KIND OF CRIMES Criminals in the past used to have guns, masks and escape cars. Now they have a computer, a telephone and a piece of computer equipment called a modem. They simply dial a telephone number to link their own computer with the others, and then, using a password (a secrete word or phrase), enter a company's computer system (for example, in a bank or a government office). In 1999 two American teenagers broke into a computer system and added rude messages to some information and made other important data disappear. The damage cost over two million dollars to correct. A 12-year old boy in Detroit used his own computer to enter the computer system of a large company and caused financial chaos. In Britain, computer crime costs companies about 400 million pounds a year. Often, the computer criminals do not want to make money; they just want to show the world how clever they are. They also like creating computer viruses. They program a computer disc with a special fault in it. When a computer copies the disc, the fault enters the computer's memory. That means it gets onto any other disc each time you put a new disc into your computer. Some viruses are just silly messages. For example, one puts the message «peace and love» on your computer screen while you are working. Other viruses use all the ‘memory on the computer’, and the computer is sick and unable to work. A hospital in Britain recently lost all of its records about sick patients because of a computer virus. Task 9. Answer the following questions: 1. What kind of people do you think write computer viruses? Why do they do it? 2. In what way should computer criminals be punished? 3. Have you ever faced the problem of computer viruses? 4. What influence can a virus have on your computer? Task 10. Find synonyms and antonyms for the following words in the text. The words are given in the same order as in the text:
Task 11. Match the following words from the text with their definitions:
Task 12. Read this article about a computer infection. a) Fill in the gaps with the following words and word combinations putting them in the right place: -BotNet -spyware -worm -keylogger -pharming -zombies -denial of service -identity theft Conficker has been in the news a lot recently. It is a (1)………, which unlike a virus does not need to be attached to an existing program to infect a machine, and which seems to receive regularly updated instructions from its controllers. It has created a (2)…….. – a network of infected machines. Once infected, these machines are known as (3)……. At this point no one knows what the purpose of Conficker is. At present it has infected ten million computers. These could be used for a (4)…….. attack where all the infected computers attempt to access one site simultaneously. It is probably controlled by criminals who want to steal users’ personal information, i.e (5)………… There are a number of ways of doing this: a (6)………………records information via a keyboard, (7)…………literally means harvesting users’ information while they are online. We will probably soon see if Conficker consists of this type of passive monitoring (8)…… or whether it will mount a more active attack once it receives a new set of instructions. b)The information in the article is no longer news. So, retell it in the Past Tense. NB! Conficker was first detected in November of 2008. The name Conficker is a combination of the words configuration and ficker. Task 13. Study the words:
Task 14. Read and translate text C: THE FIRST HACKERS The first "hackers" were students at the Massachusetts Institute of Technology (MIT) who belonged to the TMRC (Tech Model Railroad Club). Some of the members really built model trains. But many were more interested in the wires and circuits underneath the track platform. Spending hours at TMRC creating better circuitry was called "a mere hack." Those members who were interested in creating innovative, stylistic, and technically clever circuits called themselves (with pride) hackers. During the spring of 1959, a new course was offered at MIT, a freshman programming class. Soon the hackers of the railroad club were spending days, hours, and nights hacking away at their computer, an IBM 704. Instead of creating a better circuit, their hack became creating faster, more efficient program - with the least number of code lines. Eventually they formed a group and created the first set of hacker's rules, called the Hacker's Ethic. Steven Levy, in his book Hackers, presented the rules: Rule 1: Access to computers - and anything, which might teach you, something about the way the world works - should be unlimited and total. Rule 2: All information should be free. Rule 3: Mistrust authority - promote decentralization. Rule 4: Hackers should be judged by their hacking, not bogus criteria such as degrees, race, or position. Rule 5: You can create art and beauty on a computer. Rule 6: Computers can change your life for the better. These rules made programming at MIT's Artificial Intelligence Laboratory - a challenging, all-encompassing endeavor. Just for the exhilaration of programming, students in the Al Lab would write a new program to perform even the smallest tasks. The program would be made available to others who would try to perform the same task with fewer instructions. (5) Hackers were given free regime on the computer by two AI Lab professors, "Uncle" John McCarthy and Marvin Minsky, who realized that hacking created new insights. Over the years, the AI Lab created many innovations: LIFE, a game about survival; LISP, a new kind of programming language; the first computer chess game; The CAVE, the first computer adventure; and SPACEWAR, the first video game. Task 15. Answer the following questions: 1. Who were the first hackers? 2. Where was the new course of programming offered in spring 1953? 3.Who presented the rules for the hacker? 4. Did these rules make programming at MIT's Artificial Intelligence Laboratory - a challenging, all-encompassing endeavor? 5. Were Hackers given free regime on the computer by two AI Lab professors, "Uncle" John McCarthy and Marvin Minsky? 6. What innovations did AI Lab create? 7. Can computers change your life for the better? Task 16.Find synonyms and antonyms for the following words in the text. The words are given in the same order as in the text:
Task 17. Match the following words from the text with their definitions:
Task 18. Find the equivalents in the text: Первые "хакеры"; эффективные программы; правила хакера, этика Хакера; доступ к компьютерам; лаборатория «Искусственного интеллекта», написать новую программу, новый вид языка программирования; компьютерная игра в шахматы; первая видео игра. Task 19.Are the sentences True or False? 1. Spending hours at TMRC (Tech Model Railroad Club) creating better circuitry was called "a mere hack." 2. Those members who were interested in creating innovative, stylistic, and technically clever circuits called themselves (with pride) hackers. 3. All MIT students were not interested in creating programs. 4. The first hackers were Tambov State University students. 5. The freshman programming class was offered at MIT in the spring of 1959. 6. They formed a group and created the first set of hacker's rules, called the Hacker's Ethic. 7. Hackers must belong to a particular race and position. |
